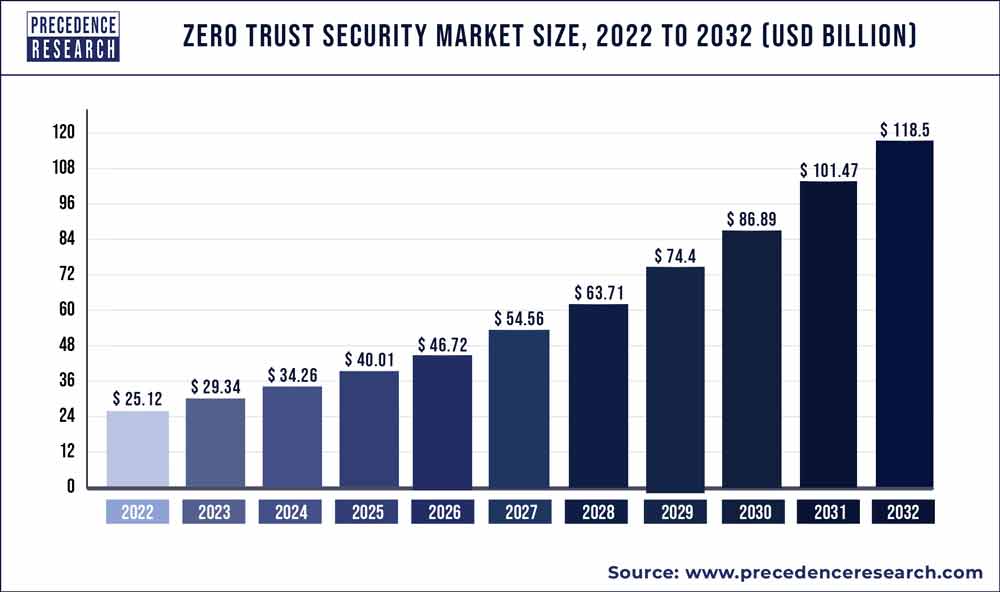
According to a recent research report titled ” Zero Trust Security Market (By Authentication Types: Single-factor Authentication, Multi-factor Authentication; By Solution Type: Network Security, Data Security, Endpoint Security, API Security, Cloud Security, Others; By Deployment Type: Cloud, On-Premises) – Global Industry Analysis, Size, Share, Growth, Trends, Regional Outlook, and Forecast 2023-2032″ published by Precedence Research, the global zero trust security market size is projected to touch around USD 118.5 billion by 2032 and growing at a CAGR of 16.78% over the forecast period 2023 to 2032. This comprehensive study examines various factors and their impact on the growth of the zero trust security market.
The report primarily focuses on the volume and value of the zero trust security market at the global, regional, and company levels. At the global level, the report analyzes historical data and future prospects to present an overview of the overall market size. Regionally, the study emphasizes key regions such as North America, Europe, the Middle East & Africa, Latin America, and others.
Furthermore, the research report provides specific segmentations based on regions (countries), companies, and all market segments. This analysis offers insights into the growth and revenue trends during the historical period of 2017 to 2032, as well as the projected period. By understanding these segments, it becomes possible to identify the significance of different factors that contribute to market growth.
Download a Free Copy of Our Latest Sample Report@ https://www.precedenceresearch.com/sample/3170
The research also highlights significant progressions in both organic and inorganic growth strategies within the global zero trust security market. Numerous companies are placing emphasis on new product launches, gaining product approvals, and implementing various business expansion tactics. Moreover, the report presents detailed profiles of firms operating in the zero trust security market, along with their respective market strategies. Additionally, the study concentrates on prominent industry participants, furnishing details such as company profiles, product offerings, financial updates, and noteworthy advancements.
Zero Trust Security Market Report Scope
| Report Coverage | Details |
| Market Size in 2023 | USD 29.34 Billion |
| Market Size by 2032 | USD 118.5 Billion |
| Growth Rate from 2023 to 2032 | CAGR of 16.78% |
| Largest Market | North America |
| Base Year | 2022 |
| Forecast Period | 2023 To 2032 |
| Segments Covered | By Authentication Types, By Solution Type, and By Deployment Type |
| Regions Covered | North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa |
Also read: Cardiovascular Digital Solutions Market Size to Record US$ 183.23 Billion by 2032
Major Key Points Covered in Report:
Executive Summary: It includes key trends of the electric vehicle fuel cell market related to products, applications, and other crucial factors. It also provides analysis of the competitive landscape and CAGR and market size of the electric vehicle fuel cell market based on production and revenue.
Production and Consumption by Region: It covers all regional markets to which the research study relates. Prices and key players in addition to production and consumption in each regional market are discussed.
Key Players: Here, the report throws light on financial ratios, pricing structure, production cost, gross profit, sales volume, revenue, and gross margin of leading and prominent companies competing in the Electric vehicle fuel cell market.
Market Segments: This part of the report discusses product, application and other segments of the electric vehicle fuel cell market based on market share, CAGR, market size, and various other factors.
Research Methodology: This section discusses the research methodology and approach used to prepare the report. It covers data triangulation, market breakdown, market size estimation, and research design and/or programs.
Market Key Players
The report incorporates company profiles of key players in the market. These profiles encompass vital information such as product portfolio, key strategies, and a comprehensive SWOT analysis for each player. Additionally, the report presents a matrix illustrating the presence of each prominent player, enabling readers to gain actionable insights. This facilitates a thoughtful assessment of the market status and aids in predicting the level of competition in the zero trust security market.
Some of the prominent players in the zero trust security market include
- Cisco Systems, Inc.
- Palo Alto Networks, Inc.
- Microsoft Corporation
- Symantec Corporation (now part of Broadcom Inc.)
- Okta, Inc.
- IBM Corporation
- Check Point Software Technologies Ltd.
- Akamai Technologies, Inc.
- Fortinet, Inc.
- CyberArk Software Ltd.
Zero Trust Security Market Segmentations
By Authentication Types
- Single-factor Authentication
- Multi-factor Authentication
By Solution Type
- Network Security
- Data Security
- Endpoint Security
- API Security
- Cloud Security
- Others
By Deployment Type
- Cloud
- On-Premises
By Geography
- North America
- Europe
- Asia-Pacific
- Latin America
- Middle East and Africa
Why should you invest in this report?
This report presents a compelling investment opportunity for those interested in the global zero trust security market. It serves as an extensive and informative guide, offering clear insights into this niche market. By delving into the report, you will gain a comprehensive understanding of the various major application areas for zero trust security. Furthermore, it provides crucial information about the key regions worldwide that are expected to experience substantial growth within the forecast period of 2023-2030. Armed with this knowledge, you can strategically plan your market entry approaches.
Moreover, this report offers a deep analysis of the competitive landscape, equipping you with valuable insights into the level of competition prevalent in this highly competitive market. If you are already an established player, it will enable you to assess the strategies employed by your competitors, allowing you to stay ahead as market leaders. For newcomers entering this market, the extensive data provided in this report is invaluable, providing a solid foundation for informed decision-making.
Some of the key questions answered in this report:
- What is the size of the overall Zero trust security market and its segments?
- What are the key segments and sub-segments in the market?
- What are the key drivers, restraints, opportunities and challenges of the Zero trust security market and how they are expected to impact the market?
- What are the attractive investment opportunities within the Zero trust security market?
- What is the Zero trust security market size at the regional and country-level?
- Who are the key market players and their key competitors?
- What are the strategies for growth adopted by the key players in Zero trust security market?
- What are the recent trends in Zero trust security market? (M&A, partnerships, new product developments, expansions)?
- What are the challenges to the Zero trust security market growth?
- What are the key market trends impacting the growth of Zero trust security market?
Table of Content:
Chapter 1. Introduction
1.1. Research Objective
1.2. Scope of the Study
1.3. Definition
Chapter 2. Research Methodology (Premium Insights)
2.1. Research Approach
2.2. Data Sources
2.3. Assumptions & Limitations
Chapter 3. Executive Summary
3.1. Market Snapshot
Chapter 4. Market Variables and Scope
4.1. Introduction
4.2. Market Classification and Scope
4.3. Industry Value Chain Analysis
4.3.1. Raw Material Procurement Analysis
4.3.2. Sales and Distribution Channel Analysis
4.3.3. Downstream Buyer Analysis
Chapter 5. COVID 19 Impact on Zero Trust Security Market
5.1. COVID-19 Landscape: Zero Trust Security Industry Impact
5.2. COVID 19 – Impact Assessment for the Industry
5.3. COVID 19 Impact: Global Major Government Policy
5.4. Market Trends and Opportunities in the COVID-19 Landscape
Chapter 6. Market Dynamics Analysis and Trends
6.1. Market Dynamics
6.1.1. Market Drivers
6.1.2. Market Restraints
6.1.3. Market Opportunities
6.2. Porter’s Five Forces Analysis
6.2.1. Bargaining power of suppliers
6.2.2. Bargaining power of buyers
6.2.3. Threat of substitute
6.2.4. Threat of new entrants
6.2.5. Degree of competition
Chapter 7. Competitive Landscape
7.1.1. Company Market Share/Positioning Analysis
7.1.2. Key Strategies Adopted by Players
7.1.3. Vendor Landscape
7.1.3.1. List of Suppliers
7.1.3.2. List of Buyers
Chapter 8. Global Zero Trust Security Market, By Authentication Types
8.1. Zero Trust Security Market, by Authentication Types, 2023-2032
8.1.1 Single-factor Authentication
8.1.1.1. Market Revenue and Forecast (2020-2032)
8.1.2. Multi-factor Authentication
8.1.2.1. Market Revenue and Forecast (2020-2032)
Chapter 9. Global Zero Trust Security Market, By Solution Type
9.1. Zero Trust Security Market, by Solution Type, 2023-2032
9.1.1. Network Security
9.1.1.1. Market Revenue and Forecast (2020-2032)
9.1.2. Data Security
9.1.2.1. Market Revenue and Forecast (2020-2032)
9.1.3. Endpoint Security
9.1.3.1. Market Revenue and Forecast (2020-2032)
9.1.4. API Security
9.1.4.1. Market Revenue and Forecast (2020-2032)
9.1.5. Cloud Security
9.1.5.1. Market Revenue and Forecast (2020-2032)
9.1.6. Others
9.1.6.1. Market Revenue and Forecast (2020-2032)
Chapter 10. Global Zero Trust Security Market, By Deployment Type
10.1. Zero Trust Security Market, by Deployment Type, 2023-2032
10.1.1. Cloud
10.1.1.1. Market Revenue and Forecast (2020-2032)
10.1.2. On-Premises
10.1.2.1. Market Revenue and Forecast (2020-2032)
Chapter 11. Global Zero Trust Security Market, Regional Estimates and Trend Forecast
11.1. North America
11.1.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.1.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.1.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.1.4. U.S.
11.1.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.1.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.1.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.1.5. Rest of North America
11.1.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.1.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.1.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2. Europe
11.2.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.4. UK
11.2.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.5. Germany
11.2.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.6. France
11.2.6.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.6.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.6.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.7. Rest of Europe
11.2.7.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.7.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.7.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3. APAC
11.3.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.4. India
11.3.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.5. China
11.3.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.6. Japan
11.3.6.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.6.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.6.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.7. Rest of APAC
11.3.7.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.7.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.7.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4. MEA
11.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.4. GCC
11.4.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.5. North Africa
11.4.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.6. South Africa
11.4.6.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.6.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.6.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.7. Rest of MEA
11.4.7.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.7.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.7.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.5. Latin America
11.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.5.4. Brazil
11.5.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.5.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.5.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.5.5. Rest of LATAM
11.5.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.5.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.5.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
Chapter 12. Company Profiles
12.1. Cisco Systems, Inc.
12.1.1. Company Overview
12.1.2. Product Offerings
12.1.3. Financial Performance
12.1.4. Recent Initiatives
12.2. Palo Alto Networks, Inc.
12.2.1. Company Overview
12.2.2. Product Offerings
12.2.3. Financial Performance
12.2.4. Recent Initiatives
12.3. Microsoft Corporation
12.3.1. Company Overview
12.3.2. Product Offerings
12.3.3. Financial Performance
12.3.4. Recent Initiatives
12.4. Symantec Corporation (now part of Broadcom Inc.)
12.4.1. Company Overview
12.4.2. Product Offerings
12.4.3. Financial Performance
12.4.4. Recent Initiatives
12.5. Okta, Inc.
12.5.1. Company Overview
12.5.2. Product Offerings
12.5.3. Financial Performance
12.5.4. Recent Initiatives
12.6. IBM Corporation
12.6.1. Company Overview
12.6.2. Product Offerings
12.6.3. Financial Performance
12.6.4. Recent Initiatives
12.7. Check Point Software Technologies Ltd.
12.7.1. Company Overview
12.7.2. Product Offerings
12.7.3. Financial Performance
12.7.4. Recent Initiatives
12.8. Akamai Technologies, Inc.
12.8.1. Company Overview
12.8.2. Product Offerings
12.8.3. Financial Performance
12.8.4. Recent Initiatives
12.9. Fortinet, Inc.
12.9.1. Company Overview
12.9.2. Product Offerings
12.9.3. Financial Performance
12.9.4. Recent Initiatives
12.10. CyberArk Software Ltd.
12.10.1. Company Overview
12.10.2. Product Offerings
12.10.3. Financial Performance
12.10.4. Recent Initiatives
Chapter 13. Research Methodology
13.1. Primary Research
13.2. Secondary Research
13.3. Assumptions
Chapter 14. Appendix
14.1. About Us
14.2. Glossary of Terms
Contact Us:
Mr. Alex
Sales Manager
Call: +1 9197 992 333
Email: sales@precedenceresearch.com
Web: https://www.precedenceresearch.com
Blog: https://www.pharma-geek.com